

Every day we intercept thousands of cyber threats & prevent next-generation attacks
We provide you intelligence
right from the source.
right from the source.
We filter out the noise and provide
actionable & timely insights.
actionable & timely insights.
We empower your organization with a
proactive stance against future threats.
proactive stance against future threats.
Protect your assets with our 24/7 Cyber Threat and Risk Intelligence Platforms

One Step Ahead
We detect and mitigate any cybersecurity threat or malicious activity before they can compromise you.
700+
High-End APT Groups Being Actively Monitored
Trusted Partner
We have been a trusted partner for hundreds of private and public organizations from all verticals.
2600+
The number of active platform users


Tailored Approach
We recognize your unique objectives & adapt our solutions accordingly.
9.8 billion
Raw Data Acquired from U.S.T.A. Sensors
Our Cyber Threat
Intelligence Solutions
Will Never Let You Down
Our Products
Our cyber threat intelligence platform U.S.T.A. provides intelligence-led insights from adversarial sources. Thanks to our curated data collection tools and detection mechanisms, we keep our watch on all layers of the digital landscape. The combination of U.S.T.A.’s main modules allows our clients to get a proactive upper hand in detecting and mitigating next-generation cyber threats.

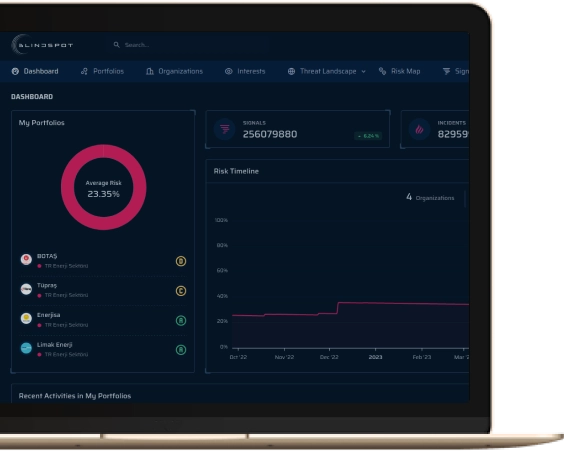
Our risk intelligence platform BLINDSPOT provides the user with a holistic assessment of any organization’s cyber risk level. BLINDSPOT is made to monitor contemporary incidents and prevent software & physical supply-chain attacks and detrimental breaches across the globe. By empowering the clients to monitor their and the suppliers’ exposure to cybercrime, we make sure there are no blind spots left.
PRODAFT offers tailored and proactive approaches against constantly evolving cyber attack techniques
Our Vision
Our vision is embedded in our name where PRODAFT stands for Proactive Defense Against Future Threats. With our mission to protect citizens, businesses and governments from major security threats by providing timely and accurate information, we elevate your security and help you mitigate threats well in advance.

Discover our resources
Organized Cyber-Crime

[01]
This report explores the operational environment of the Nomadic Octopus espionage group's Tajikistan Campaign: Paperbug.
April 14, 2023
State-sponsored Cybercrime

[02]
RIG EK is a financially-motivated program that has been active since 2014. ...
February 27, 2023
Contact Us
Questions or any cybersecurity matters you would like to discuss?
© Copyright 2024 - PRODAFT All rights reserved.

![[FIN7] Fin7 Unveiled: A deep dive into notorious cybercrime gang](/images/blog-3.webp)